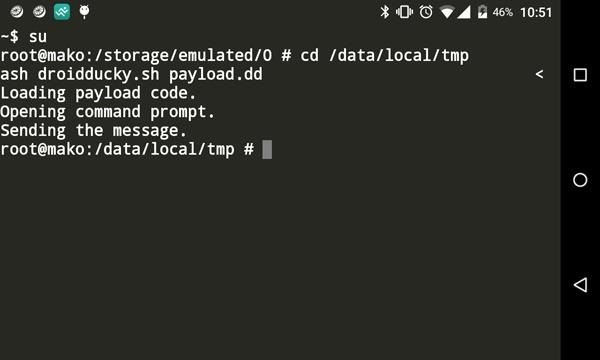
Darren Kitchen on Twitter: "Here's something crazy ⌨️💡🪞 — Stealing data OVER CAPSLOCK! Did you know keyboard LEDs are bi-directional? Keystroke Reflection is a new side-channel exfiltration attack for the NEW 🐤

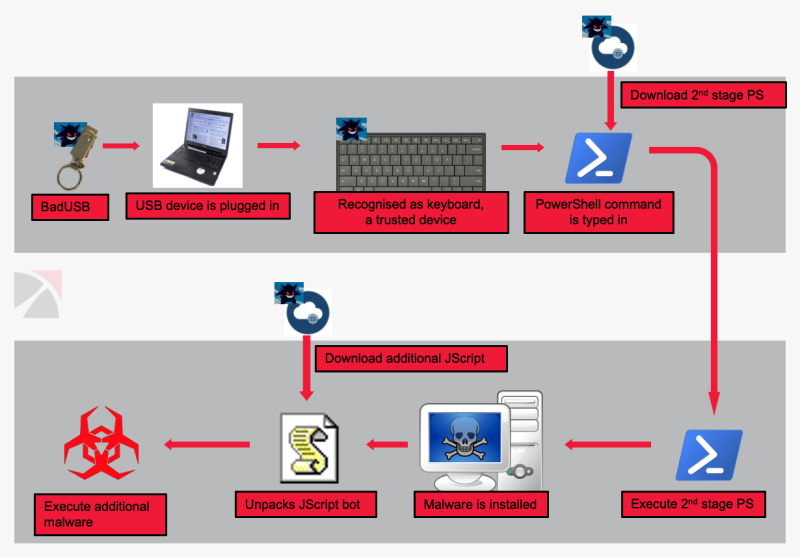
HID Attack. The external device can inject input events. The malicious... | Download Scientific Diagram

USB HID keyboard: why 4 URBs are generated for a keypress instead of 2? - Electrical Engineering Stack Exchange
GitHub - samyk/usbdriveby: USBdriveby exploits the trust of USB devices by emulating an HID keyboard and mouse, installing a cross-platform firewall-evading backdoor, and rerouting DNS within seconds of plugging it in.